After Bitcoin revolutionized digital currency, Ethereum emerged as a "second generation blockchain," aiming to decentralize a broader spectrum of financial systems, not just peer-to-peer currency transfers.
However, Ethereum’s design, constrained by the technological limitations of its time, could handle only about 15 transactions per second (TPS). For context, centralized systems like Visa were processing thousands of TPS.
While Ethereum's decentralized structure and smart contract capabilities were groundbreaking, its throughput limitations couldn't scale to meet the demands of global financial activity.
As Ethereum became the dominant platform for decentralized applications (dApps), the need for higher transaction capacity surged. This became painfully apparent during the 2017 CryptoKitties craze, where the network was clogged, and gas fees skyrocketed, showcasing the inefficiency of layer 1 blockchains.
To address this, a new wave of solutions was introduced — layer 2 blockchains, or layer 2 scaling solutions — that aim to turn Ethereum into a scalable, usable financial network for the world.
In this article we will explore what layer 2 blockchains are and their different times.
What Is A Layer 2 Blockchain Network?
Layer 2 networks are secondary frameworks or protocols built on top of existing blockchain networks (referred to as Layer 1).
The primary goal of L2s is to address the scalability challenges faced by major blockchains like Bitcoin and Ethereum, which struggle to process a high volume of transactions per second (TPS) to prioritize decentralization and security.
Read our article on the Blockchain Trilemma to learn the trade-offs between scalability, security, and decentralization.
In essence, layer 2 solutions offload a significant portion of transaction processing from the main blockchain, allowing it to focus on validation and security, while the layer 2 handles the heavy transaction load.
According to L2Beat, over $30 billion is locked in layer 2 scaling solutions in the Ethereum ecosystem alone.
A key feature of layer 2 blockchains is their ability to bundle or aggregate multiple transactions and then send them back to the layer 1 blockchain for final validation. This process reduces congestion on the main blockchain, lowering transaction fees and increasing the overall number of transactions that can be processed simultaneously.
Layer 2 Solutions Are Not Blockchains
Layer 2 solutions are not exactly blockchains in the traditional sense.
While they are often called "layer 2 blockchains," they don't operate as independent, fully-fledged blockchains like layer 1 networks such as Bitcoin or Ethereum.
Instead, they function more as extensions or enhancements of existing layer 1 blockchains, designed to handle transactions off-chain or in parallel, before anchoring their final state back onto the main chain (layer 1) for security and finality.
The key distinction lies in the fact that layer 2 solutions rely on the underlying security and decentralization of the layer 1 blockchain. They do not have their own consensus mechanism, mining or staking processes, and do not exist independently.
Due to an absence of block creation and validation mechanism, they defer to the layer 1 blockchain for security guarantees, such as transaction validity and resistance to tampering.
Layer 2 solutions, like rollups or state channels, process transactions "off-chain" to reduce congestion, but they use layer 1 for final confirmation, making them dependent on the base layer for integrity.
Different Types Of Layer 2 Scaling Solutions
Layer 2 solutions like rollups, state channels, and sidechains work by leveraging the security of the base layer while offering faster, more efficient transaction processing. This makes them a critical piece in the puzzle of scaling Ethereum and other similar blockchains.
The most popular type of layer 2 solutions are rollups, including optimistic rollups and zero-knowledge (ZK) rollups.
Rollups
Rollups are a layer 2 scaling solution that allow blockchain networks, like Ethereum, to process a large number of transactions off-chain while maintaining the security and decentralization of the main layer 1 blockchain.
They bundle or "roll up" multiple transactions off-chain and submit them to the layer 1 blockchain as a single batch, significantly reducing the load on the main chain.
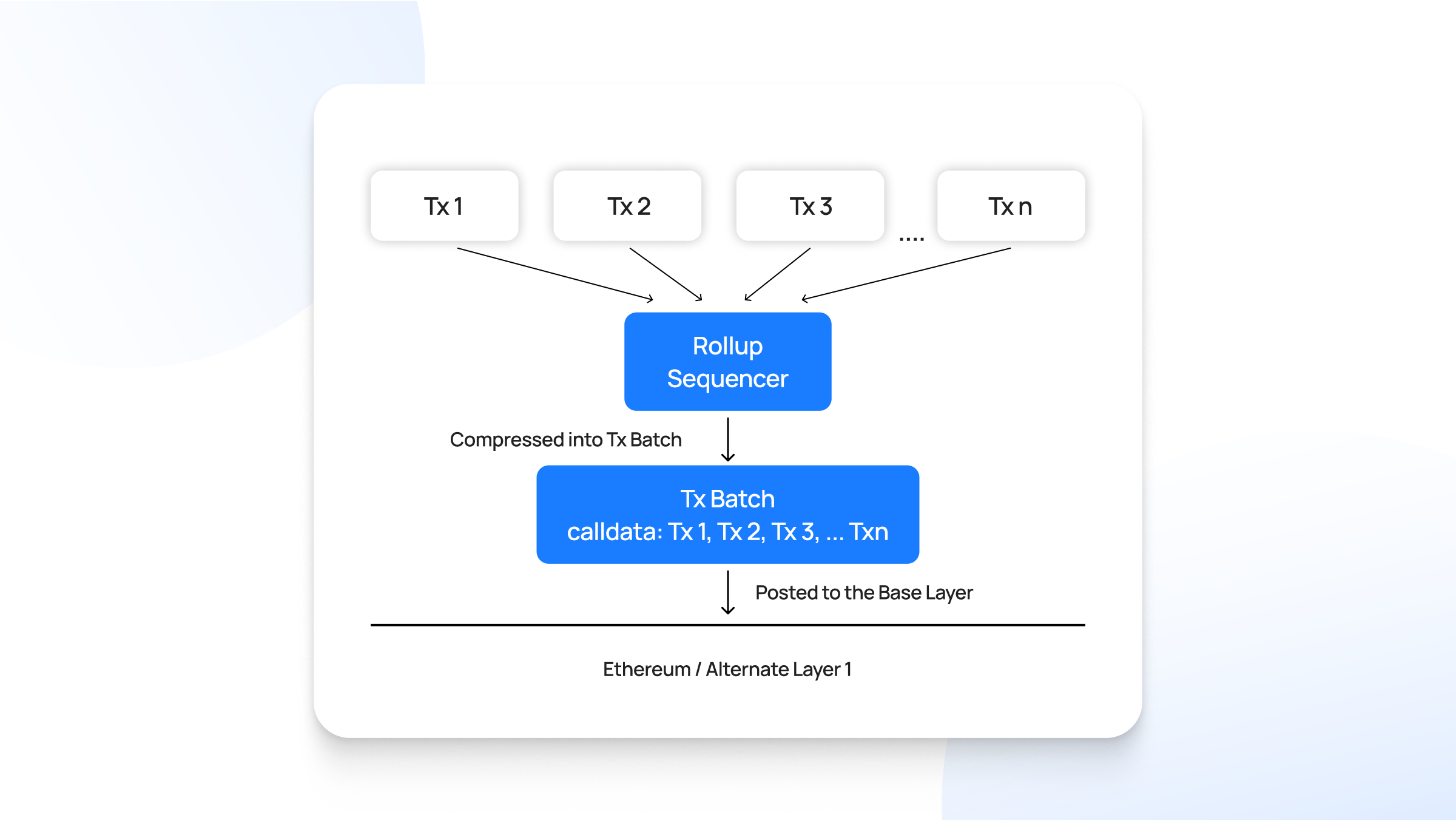
By doing this, rollups help increase transaction throughput, lower fees, and alleviate congestion, all while preserving security guarantees.
There are two primary types of rollups: Optimistic Rollups and Zero-Knowledge (ZK) Rollups, each with a distinct method for achieving scalability.
1. Optimistic Rollups
Optimistic rollups operate under the assumption that transactions are valid by default, hence the term "optimistic."
Instead of validating every transaction on-chain, they only run a validation check (via fraud proofs) if a transaction is challenged by another user. This means that the computation for validating transactions is significantly reduced, as the majority of transactions are not directly verified unless there is suspicion of fraud.
- Assumption: Transactions are assumed to be valid unless proven otherwise.
- Challenge Period: A dispute period (typically 7 days) allows anyone to challenge and prove the invalidity of transactions within a batch.
- Advantages: Faster transaction processing, simpler implementation, and compatibility with existing Ethereum smart contracts.
- Disadvantages: Longer withdrawal times due to the challenge period, potential for fraud challenges, and reliance on game theory for security.
- Examples: Arbitrum, Optimism
2. Zero-Knowledge (ZK) Rollups
ZK Rollups use cryptographic proofs known as Zero-Knowledge Proofs (specifically ZK-SNARKs or ZK-STARKs) to ensure the validity of off-chain transactions.
Instead of relying on the assumption of validity, ZK rollups generate and submit a proof (a small, compact cryptographic summary) to the layer 1 blockchain, which verifies that the off-chain transactions are valid. This eliminates the need for trust or fraud-proof mechanisms and provides near-instant finality since the proof itself guarantees correctness.
- Assumption: Transactions are assumed to be invalid until proven valid using cryptographic zero-knowledge proofs.
- Proof Generation: Complex mathematical proofs are generated to prove the validity of transactions without revealing any of the underlying data, offering enhanced privacy.
- Advantages: Near-instant transaction finality, high security, and increased privacy.
- Disadvantages: More complex implementation, potentially higher computational costs for proof generation, and may not be suitable for all types of applications.
- Examples: zkSync Era, Immutable
State Channels
State channels are bidirectional communication channels between two or more participants on a blockchain network. They allow these participants to conduct multiple transactions off-chain (i.e., outside the main blockchain) before settling the final state on the main chain.
In simpler words, state channels allow parties to transact directly with one another off-chain by opening a a private communication channel between two or more participants who wish to transact with each other without constantly interacting with the layer 1 blockchain.
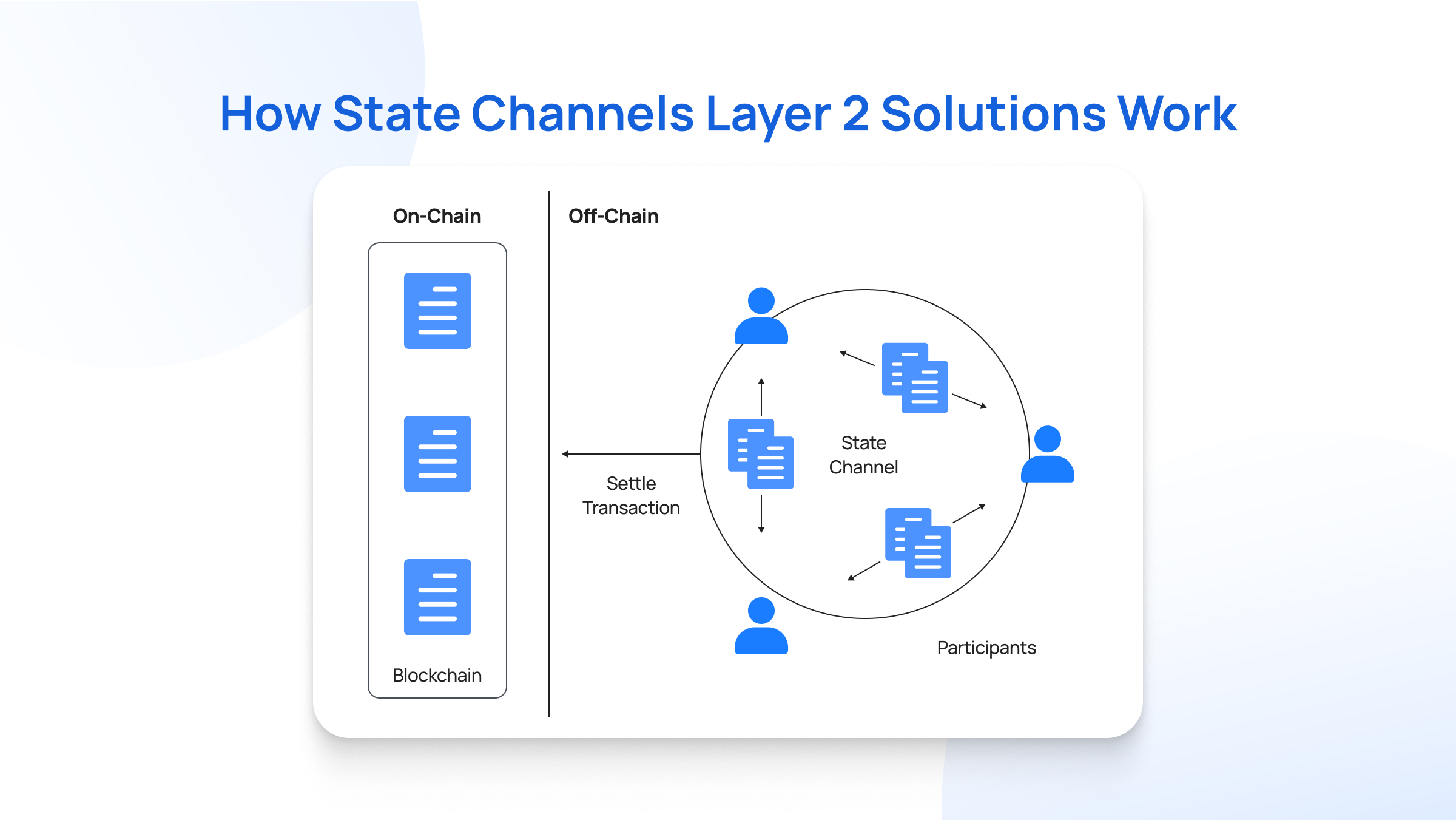
They are particularly useful for applications requiring frequent interactions between the same participants, such as gaming, micropayments, and real-time services.
State channels work on the premise that blockchains are “state machines”. This means that at any given moment, the blockchain is in a specific state (a snapshot of the participants' balances or other relevant data at a particular point in time).
The process involves three main phases:
- Opening the channel
- Off-chain interactions
- Closing the channel
Opening the Channel
To open a state channel, participants must first lock up a portion of their assets or "state" on the layer 1 blockchain in a multi-signature smart contract. This contract acts as a security mechanism, ensuring that the funds will be distributed according to the final state of the off-chain interactions.
Once the assets are locked, the participants can begin transacting off-chain without the need for further involvement from the blockchain until the channel is closed.
Off-Chain Interactions
While the channel is open, participants can exchange signed transactions between themselves directly. These transactions update the state of the channel, but they are not broadcast to the main blockchain.
Each transaction leads to a new state of the channel, which is recorded and signed (cryptographically) by all participants. This ensures everyone agrees on the current balance and ownership of assets within the channel.
As long as both (or all) parties agree, they can transact an unlimited number of times without incurring any blockchain transaction fees.
For example, in a state channel used for payments, one party might incrementally pay the other small amounts over time, updating the balance with each transaction. However, none of these transactions are recorded on the main blockchain.
Closing the Channel
When participants want to end their interactions or withdraw their funds, they submit the final state of the channel to the layer 1 blockchain.
The smart contract verifies the final state, ensuring that the distribution of assets is correct according to the signed transactions. Once verified, the contract releases the funds according to the final agreed-upon state.
In the case of disputes, the channel can be closed at any time by either participant, and the layer 1 blockchain will determine the final state based on the last valid signed transaction.
Validiums
Validiums represent a unique type of Layer 2 scaling solution that combines elements of zero-knowledge rollups (zkRollups) with off-chain data availability.
Validiums are especially well-suited for applications requiring high throughput but where decentralization and data availability on-chain are not the primary concerns, such as gaming, NFTs, and specific enterprise use cases.
.png)
Validiums share some key similarities with zero-knowledge (ZK) rollups in terms of security architecture. Both rely on zero-knowledge proofs (ZKPs) to ensure the validity of off-chain transactions without having to store all the transaction data on the layer 1 blockchain. However, Validiums differ from ZK-rollups in how they handle data availability.
- Off-Chain Data Storage: Validiums store the bulk of their transaction data off-chain, rather than recording it on the layer 1 blockchain like ZK-rollups. This allows Validiums to scale to a much greater degree, as they are not constrained by the data storage limits of the base layer. The off-chain data is typically stored by a trusted set of data providers or validators.
- Zero-Knowledge Proofs for Security: While transaction data is stored off-chain, Validiums still use ZKPs to ensure that all transactions are valid. These cryptographic proofs are submitted to the layer 1 blockchain (such as Ethereum) for verification.
StarkEx is a prominent example of a Validium solution developed by StarkWare. It is used to power several decentralized exchanges (DEXs) and other applications, offering high scalability and low transaction fees.
Sidechains: An Exception
Sidechains are often discussed in the context of layer 2 scaling solutions, but they differ fundamentally from other layer 2 technologies like rollups or state channels because they are not technically built "on top" of a layer 1 blockchain. Instead, sidechains function as independent blockchains that run in parallel to the main chain (layer 1), such as Ethereum or Bitcoin.
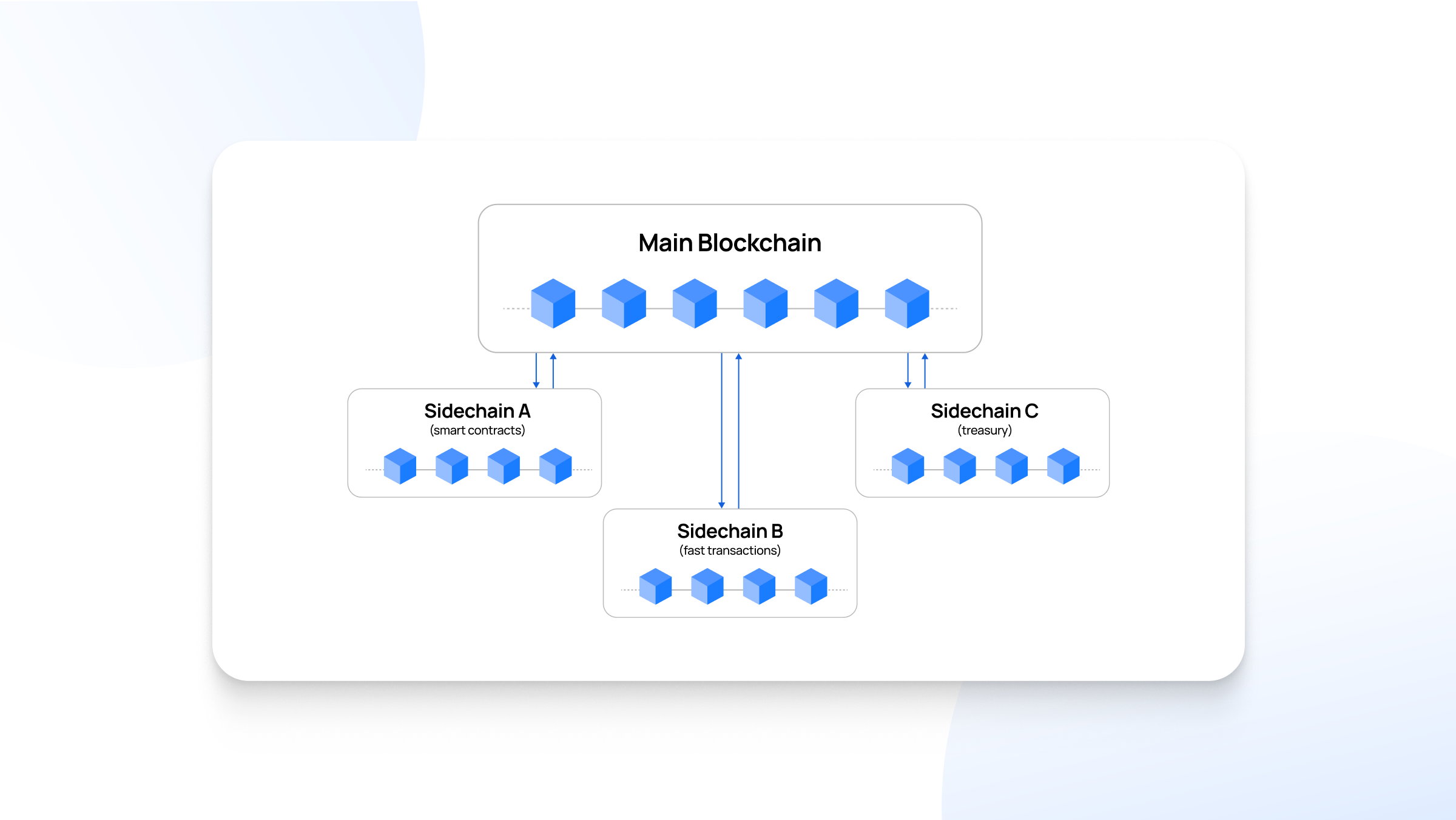
Sidechains are designed to offer a more scalable environment for transactions and smart contracts, addressing issues like high fees and slow transaction times seen on the main chain. Read on to know how they generally work.
Two-Way Bridge
A sidechain is linked to the main blockchain through a two-way bridge.
This bridge allows users to transfer assets (such as tokens) from the main chain to the sidechain and back. For example, a user can lock some of their Ether (ETH) on the Ethereum main chain, and an equivalent amount of tokens will be made available on the sidechain for use.
The bridge locks the assets on the main chain and "mirrors" them on the sidechain, ensuring the total supply of tokens remains the same across both chains.
Independent Consensus
One key feature of sidechains is that they have their own consensus mechanisms, separate from the main chain.
For example, while Ethereum may use Proof of Stake (PoS) as its consensus algorithm, a sidechain might use a different mechanism, such as Delegated Proof of Stake (DPoS) or Proof of Authority (PoA).
This independence allows sidechains to optimize for different trade-offs in terms of speed, scalability, and cost, which can differ from the priorities of the layer 1 chain.
Transaction Processing
Once assets are transferred to the sidechain, users can interact with smart contracts, execute transactions, and participate in dApps on the sidechain without involving the main blockchain.
Transactions on the sidechain are processed according to its consensus rules, typically at much higher throughput and lower cost than the main chain.
Periodically, or when users wish to withdraw their assets back to the main chain, the sidechain will send a batch of finalized transactions through the bridge to ensure that the asset balances on the main chain are updated accordingly.
L2s Are More Important Than Most Think
Layer 2 solutions, especially rollups, have become integral to Ethereum's scaling strategy as it continues its journey toward mass adoption. Ethereum, often described as the "world computer," has struggled with scalability issues, such as limited transaction throughput and high gas fees.
To address these challenges, Ethereum has adopted what is known as a "rollup-centric roadmap", placing rollups at the center of its strategy for scaling the network without compromising on decentralization or security.
The Ethereum 2.0 upgrade, which includes the transition to Proof of Stake (PoS) and sharding, aims to improve scalability. However, these upgrades alone cannot fully address the issue.
Ethereum’s base layer was not designed to handle the transaction volumes needed for global mass adoption without sacrificing decentralization or security. This is where layer 2 solutions, particularly rollups, come into play.
The Rollup-Centric Roadmap
The idea of a rollup-cetric roadmap is to offload the majority of transaction processing rollups, while Ethereum’s base layer (layer 1) focuses primarily on security, consensus, and data availability.
This strategy enables Ethereum to scale massively without compromising its decentralized nature.
Rollups are currently seen as the most promising scaling solution because they provide a way to increase transaction throughput while leveraging Ethereum’s existing security model. In a rollup-centric roadmap, Ethereum’s layer 1 serves as a settlement layer, ensuring that transactions processed on layer 2 are valid and secure.
The rollup-centric approach has several key advantages.
Layer 1 for settlement and data availability
Ethereum’s base layer will primarily ensure that data related to off-chain transactions is stored and accessible in a secure and decentralized manner.
This preserves Ethereum’s security and decentralization while making it possible to scale transaction throughput via rollups.
Modular blockchain Architecture
The rollup-centric approach creates a modular blockchain architecture. In this model, the execution of transactions (via rollups) is separated from the consensus and data availability layers (handled by Ethereum’s base layer).
This modularity allows for each component to be optimized independently.
Rollups can focus on increasing scalability and reducing transaction costs, while Ethereum’s main chain continues to provide robust security.
Composability and Interoperability
One of Ethereum’s biggest strengths is its composability — the ability of smart contracts to interact seamlessly with one another.
In a rollup-centric Ethereum, this composability is preserved because rollups are still linked to the same layer 1 blockchain.
As a result, dApps can continue to work together, whether they’re on Ethereum’s base layer or a rollup.
ZK-Rollups and zkEVM
Ethereum’s rollup-centric roadmap places a special emphasis on ZK-Rollups because they offer instant transaction finality, higher security, and lower latency compared to optimistic rollups.
Moreover, the development of zkEVMs like StarkNet and zkSync is a key part of Ethereum’s future vision. zkEVMs will allow developers to deploy smart contracts on ZK-rollups that are fully compatible with Ethereum’s infrastructure, enabling seamless interaction between the main chain and the rollup.
Layer 1 vs Layer 2: Differences Summed Up
Feature |
Layer 1 Blockchain |
Layer 2 Blockchain |
|
Purpose |
Base layer, provides security & decentralization |
Improves scalability of the base layer (L1) |
|
Transaction Processing |
On-chain, directly on the base layer |
Off-chain or in parallel, then anchored to L1 |
|
Consensus |
Has its own independent consensus mechanism (PoW, PoS, etc.) |
Relies on the security and consensus of L1 |
|
Scalability |
Limited by the base layer's throughput |
Significantly higher throughput & lower fees |
|
Security |
Provides the highest level of security for the network |
Inherits security from L1, may have additional security measures |
|
Examples |
Bitcoin, Ethereum, Cardano |
Rollups (Optimistic & ZK), State Channels, Sidechains |
|
Relationship to L1 |
The foundation on which L2 solutions are built |
An extension or enhancement of L1 to improve performance |
Start Your L2 Journey With Transak
Embarking on your layer 2 journey is now easier than ever with Transak, the leading fiat-to-crypto on-ramp and off-ramp.
Whether you're an experienced user or just starting out, Transak offers a seamless way to access and utilize layer 2 solutions directly from your bank account or preferred payment method.
Here's how you can get started with layer 2 using Transak:
- Choose your layer 2: Transak supports a growing list of popular Layer 2 solutions, including Arbitrum, Soneium, and Polygon. Select the network that best suits your needs and preferences.
- Purchase crypto: Enter the amount of fiat currency you want to convert and select the cryptocurrency you wish to acquire on your chosen layer 2 network.
- Select your payment method: Choose your preferred payment method, such as a bank transfer, credit/debit card,or other local payment options available in your region.
- Complete the transaction: Follow the simple on-screen instructions to complete your purchase. Transak will handle the conversion and transfer the acquired cryptocurrency directly to your wallet address.
Remember: Always conduct thorough research and choose a reputable platform like Transak when dealing with cryptocurrency transactions.
Conclusion
Layer 2 solutions are not the only way to improve blockchain scalability. There are other ways too, like changes in consensus mechanism, sharding, etc.
However, making changes to the base layer is a much more tedious process and may even increase the complexity. The increased complexity could result in a larger attack surface that would compromise the integrity of the base layer.
L2s on the other hand can be upgraded (or downgraded) easily by developers. Compromised layer 2 solutions can also be kept from settling transactions on the base layer because they derive security guarantees from the latter.
Over time, we can expect to see more layer 2 solutions emerge, specifically appchains (application-specific blockchains), which are tailored to a particular use case.