We have come a long way since Satoshi Nakamoto first introduced Bitcoin in 2008. The biggest strides have been in usability and accessibility of cryptocurrencies. Security, as always, has been rock solid.
These innovations (cryptocurrencies and blockchain) have disrupted financial transactions for the better, offering a level of decentralization, speed, and transparency previously unseen.
However, this innovative landscape is not without its pitfalls. While security at the grass roots level is strong, there are other jerry rigged tech stacks and user actions that compromise asset ownership.
Among the various security challenges faced by crypto users, one particularly insidious threat is the rise of "address poisoning" attacks, which prey on the negligence of users.
It is not a malware or a brute force attack. Rather, a clever and strategic maneuver exploiting the subtleties of human behavior and the complexity inherent in the crypto ecosystem.
In this article, we take a look at what are address poisoning attacks, and how you can steer clear of them.
What Are Address Poisoning Attacks?
Address poisoning is quite a tricky issue in the crypto space. It's a kind of attack where someone watches a blockchain for transactions, then sends a small amount of crypto to an address that looks very similar to the original one.
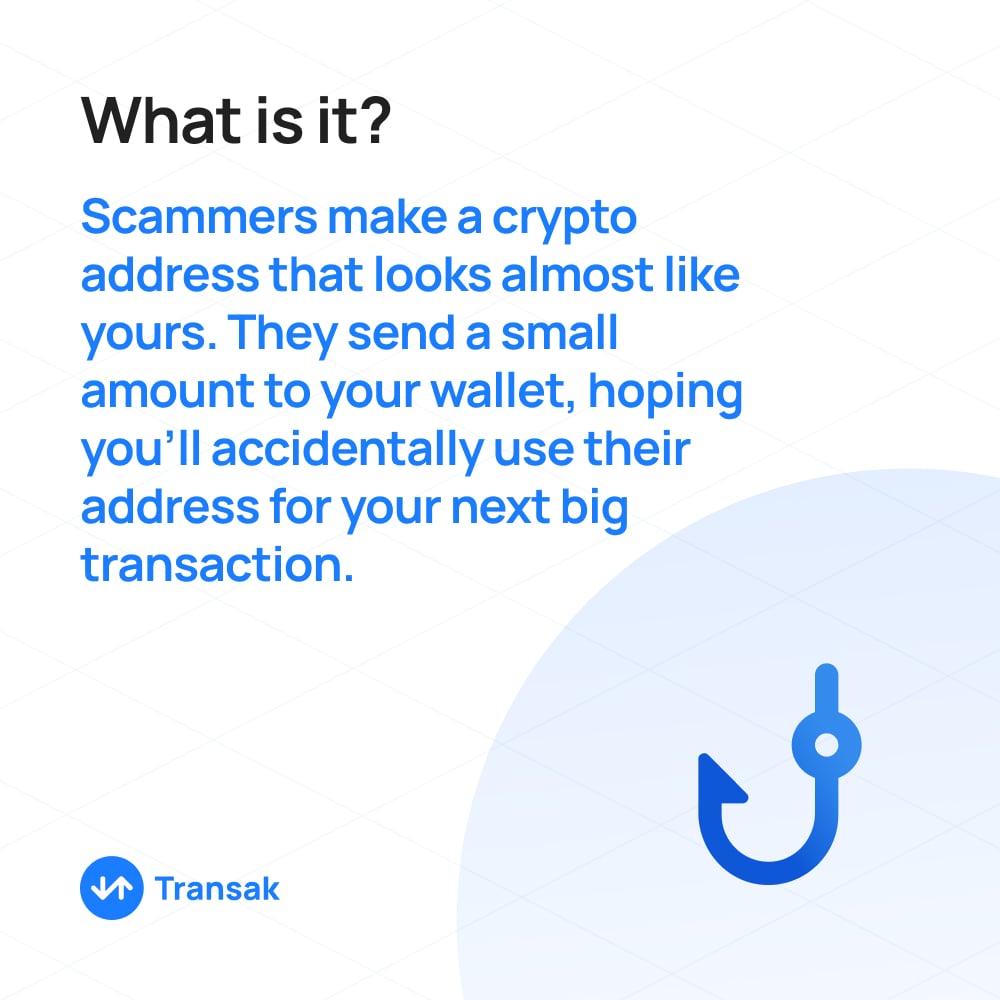
The idea is that when the original owner tries to send more crypto, they might accidentally use the wrong, similar-looking address. It's like a scammer trying to catch funds by confusing people.
The mechanics are simple yet effective.
This kind of attack relies heavily on human error, like not checking the full address carefully before sending crypto. It's sneaky because blockchain transactions can't be reversed. Once the crypto is sent to the wrong address, it's usually gone for good.
The impact of such attacks extends beyond individual financial loss. They shake the foundation of trust that underpins the digital asset ecosystem and raise serious questions about the safety and reliability of conducting transactions in this otherwise promising space.
Understanding Address Poisoning Attacks: A Detailed Breakdown
Before getting into the specifics of address poisoning, it's crucial to grasp how cryptocurrency addresses function. A cryptocurrency address is a string of letters and numbers, functioning as a destination point for sending or receiving digital assets. Due to their length and complexity, these addresses are not only difficult to remember but also challenging to verify at a glance.
The Modus Operandi
Creation of Similar-looking Addresses
Attackers keenly observe transactions on the blockchain. This is possible because the blockchain is essentially a public ledger.
You, too, can do this for free with a blockchain explorer!
That is why these attacks typically happen on public/permissionless blockchains like Bitcoin and Ethereum, rather than on permissioned enterprise blockchains. If an address poisoning attack happens on a permissioned blockchain, it is much easier to get hold of the malicious actor.
The malicious actors then generate a new address, altering just a few characters to closely resemble a legitimate address used in a transaction.
For instance, consider an Ethereum address such as 0x12f46f…12345. An attacker might create a new address that is strikingly similar, such as 0x12f45e…22345. Notice how the first four and last four digits are the same. Such subtle differences, easily overlooked at a glance, are the crux of an address poisoning attack.
There are tools that help generate such addresses. Vanity-ETH is an example.
Small Transactions to Gain Trust
To initiate an address poisoning attack, the scammer might send a small amount of cryptocurrency to the victim's crypto wallet.
This action positions their similar-looking address in the recipient's transaction history, camouflaged among genuine transactions.
Exploiting Human Error
When the victim later initiates a transaction, there's a chance they might select the scammer's address instead of the intended one.
This mistake usually happens due to the visual similarity between the addresses and often occurs when the user is copying and pasting addresses or not verifying them entirely.
Why It’s Effective
The human brain is not wired to easily distinguish between strings of random characters, making it easy to overlook minor differences in long cryptocurrency addresses.
Further, attackers often use automated scripts to generate and monitor addresses, scaling up their efforts to trick more victims. So, even if most people spot the anomaly in the address, there is a high chance that a few will fall through the trapdoor.
Unlike traditional bank transfers, blockchain transactions are irreversible. Therefore, once the crypto assets are sent to the wrong address, retrieving them is nearly impossible.
Address Poisoning vs. Other Crypto Scams
Address poisoning, while unique in its approach, is just one of the many types of scams and fraudulent activities prevalent in the cryptocurrency world.
Understanding how it differs from other scams can help users better prepare and protect their digital assets.
Common Crypto Scams
- Phishing Attacks: Unlike address poisoning, which is passive and relies on a victim's mistake, phishing is an active scam. It typically involves tricking the victim into revealing sensitive information like private keys or wallet passwords, often through fake websites or misleading emails.
- Rug Pulls: This scam is common in the decentralized finance (DeFi) space, where developers create a new cryptocurrency, hype it up, then vanish with the investors' money. Rug pulls are deceptive at the project level, in contrast to the transactional trickery of address poisoning.
- Ponzi and Pyramid Schemes: These age-old frauds have also found their way into crypto. They promise high returns for new investments but pay profits to earlier investors using the capital from newer investors, unlike address poisoning, which directly targets the transaction process.
Key Differences
- Target and Method: Address poisoning specifically targets the act of sending cryptocurrencies, leveraging the user's inattentiveness or oversight. Other scams often involve broader strategies affecting either the wallet's security directly or the investment's integrity.
- Subtlety and Detection: Address poisoning can be more difficult to detect since it doesn’t involve direct interaction with the victim or overtly fraudulent behavior. This subtlety is a stark contrast to more aggressive tactics like phishing or rug pulls.
- Preventative Measures: The measures to prevent address poisoning are different, focusing primarily on meticulous attention during transactions, compared to broader cybersecurity practices needed against phishing or the careful investment analysis required to avoid rug pulls and Ponzi schemes.
How To Avoid Address Poisoning Attacks
Address poisoning thrives on the subtlety of its execution and the potential oversight by crypto users.
Protecting yourself from such attacks requires a combination of careful practices, technological aids, and a mindset of constant vigilance.
But it's not as complicated as it may seem. Here are a few tips to stay safe.
Thoroughly Verify Addresses
Always check the entire address character by character when sending or receiving crypto. While this might seem tedious, especially with the length and complexity of blockchain addresses, it's crucial for safety.
Use QR Codes or NFT Domain Names
Addresses can be up to 64 characters long. You will probably have a headache than get scammed trying to cross-reference every character, every time.
For physical transactions or when transferring between your devices, use QR codes instead of manually typing or copy-pasting addresses. If you frequently send crypto to a specific address, save their QR code somewhere you can access easily.
Alternatively, NFT domain names like ENS domains or Unstoppable domains are human readable. If there’s any anomaly in the domain, you will be able to spot it easily in most cases.
Leverage Wallet Features
Use the address book feature in your crypto wallet. Pre-saving and labeling the addresses of frequent contacts can minimize the risk of selecting a fraudulent address.
Some wallets allow you to nickname addresses, making it easier to identify the correct recipient.
Be Cautious with Copy-Paste
Malware that alters clipboard content can replace copied addresses with the attacker’s. Always recheck the address after pasting.
Consider typing out a few characters manually after pasting to ensure the address hasn't been swapped.
Maintain Software Hygiene
Many users refrain from updating the apps on their mobile devices due to low storage, internet data consumption, and other such reasons. However, this can turn out to be a bad idea for crypto wallet apps.
Regular updates for crypto wallet apps include patches for security vulnerabilities that might expose you to address poisoning. Timely updating them ensures you are actively closing off any loopholes for malicious actors.
Use reliable security and malware detection software, especially programs that can alert you to clipboard manipulations or other suspicious activities.
Practice Transaction Discipline
When sending a large amount, first send a small amount to confirm that the address is correct.
Develop a habit of confirming the transaction details with the recipient through a separate communication channel, especially for significant transactions.
Conclusion
Address poisoning attacks emerge as a subtle yet significant threat. They highlight the necessity of vigilant personal security measures in this space.
Their effectiveness lies in the simplicity of their approach, leveraging human error rather than technical loopholes.
The defense against such attacks is primarily rooted in heightened awareness and meticulous verification practices.
Employing QR codes, utilizing NFT domain names, leveraging wallet features, being cautious with the copy-paste functionality, maintaining software hygiene, and practicing disciplined transaction habits are not just strategies but essential habits for anyone navigating the cryptocurrency world.
Address poisoning is a stark reminder that in the dynamic and innovative field of cryptocurrencies, security is not just about the robustness of technology but also about the prudence and attention to detail of each user.